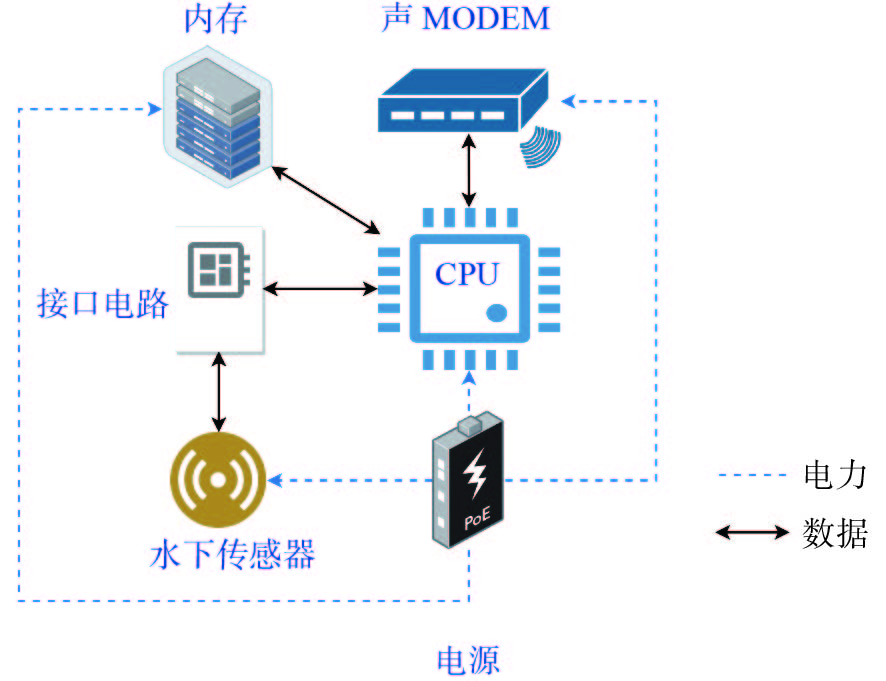
Anti-malicious Interference Technology for Underwater Wireless Sensor Networks: Applications and Recent Advances
-
摘要: 水下无线传感器网络(UWSNs)越来越广泛地应用于海洋开发等领域, 但其水声通信信道的开放性导致UWSNs容易受到水下的各类恶意干扰, 各类通信抗干扰技术可有效提高UWSNs的通信可靠性。文中首先介绍了通信抗干扰技术的发展历程及其国内外发展现状, 并对通信抗干扰技术的发展规律进行分析; 其次分析了UWSNs中通信抗干扰的关键技术以及技术需求, 最后对UWSNs通信抗干扰技术的发展应用进行了展望。Abstract: Underwater wireless sensor networks(UWSNs) are being increasingly used in marine development and other fields, but the open channels of their underwater acoustic communication makes UWSNs vulnerable to various malicious underwater interferences. Therefore, anti-interference communication technology is used to effectively improve the communication reliability of UWSNs. Accordingly, this study first introduces the development process and status of anti-interference communication technology and analyzes the law governing its development. Second, the main anti-interference communication technology used for UWSNs and the requirements of this technology are analyzed. Finally, the prospects for UWSN anti-interference communication technology are investigated.
-
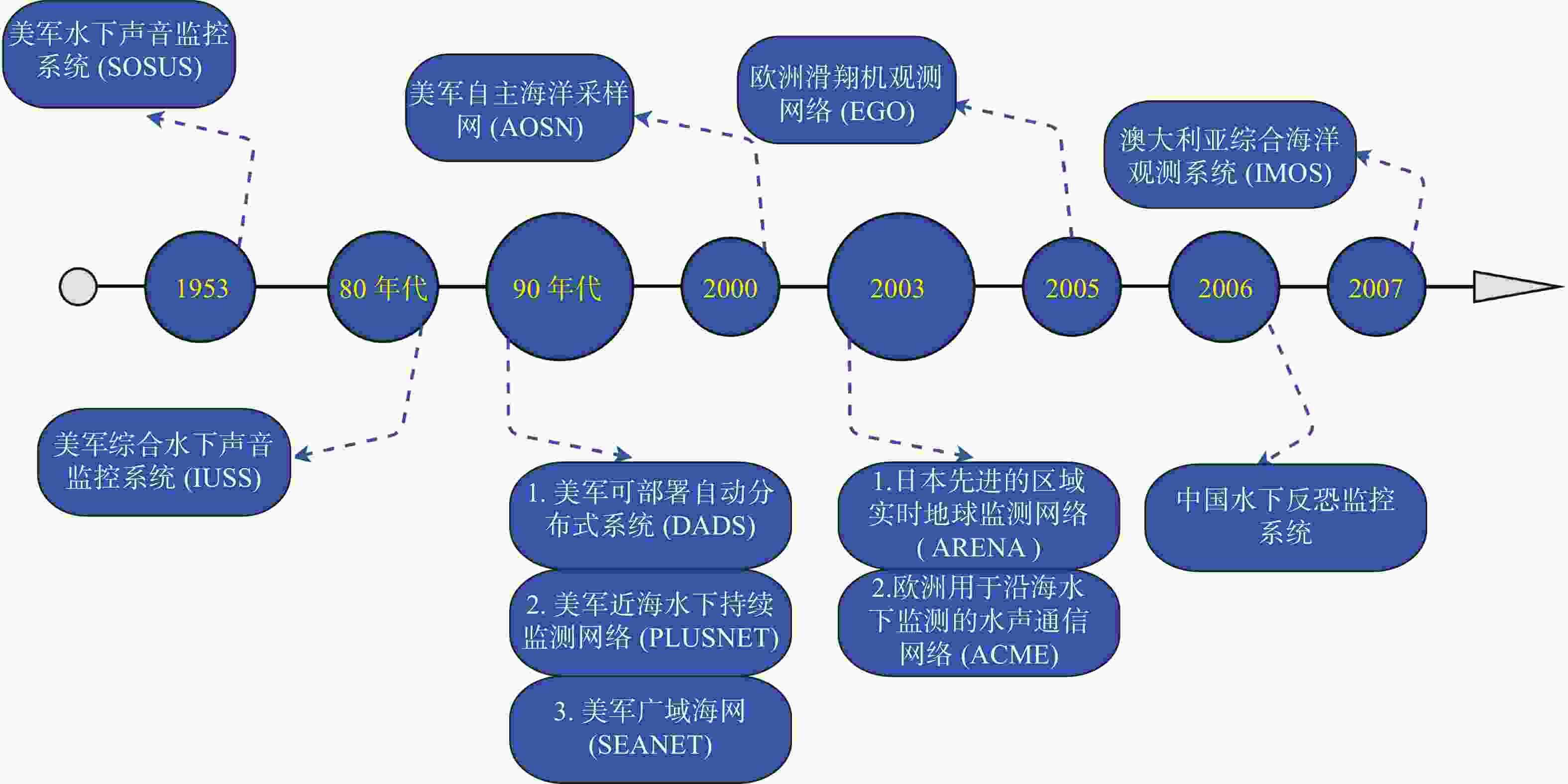
图 3 国内外水下无线传感器网络发展历程
注: 图中SOSUS为sound surveillance system; IUSS为integrated underwater surveillance system; AOSN为adaptive ocean sampling network; DADS为deployable autonomous distributed system; PLUSNET为persistent littoral undersea surveillance network; IMOS为integrated marine observing system
Figure 3. Development history of underwater wireless sensor networks at home and abroad
表 1 各国大型AUV系统型号及参数
Table 1. Models and parameters of large-scale AUV in various countries
型号系列 国家 下潜最大
深度/m最长
续航时间/h导航通信方式 “潜龙”系列 中国 6 000 40 惯性导航、铱星、超短基线、长基线、无线电、多普勒计程仪(Doppler velocity log, DVL)等 “探索”系列 中国 4 500 30 无线电、铱星、GPS定位(或声通信) “AutoSub”系列 英国 1 600 50 北极星自主导航系统 “Hugin”系列 挪威 6 000 360 惯性导航、铱星、HISAS微型导航、海上宽带无线电(marine broadband radio, MBR)通信系统、Wifi、DVL、基于星基增强系统(satellite-based augmentation system, SBAS)的GPS “Remus”系列 美国 6 000 70 高度计、惯性导航、铱星、Wifi、无线电、DVL、长基线 “Gavia”系列 中国 1 000 8 Wifi、铱星、高精度差分GPS(differential GPS, DGPS)接收机iXBlue and Kearfott的高精度DVL辅助惯导系统(inertial navigation system, INS)、超短基线、长基线 “SeaRaptorTM”系列 中国 6 000 24 Wifi、铱星、惯性导航、DVL、全球导航卫星系统(global navigation satellite system, GNSS)、超短基线、长基线 -
[1] 苏毅珊, 张贺贺, 张瑞, 等. 水下无线传感器网络安全研究综述[J]. 电子与信息学报, 2022, 44: 1-13. doi: 10.11999/JEIT221193Su Yi-shan, Zhang He-he, Zhang Rui, et al. Review of Security for Underwater Wireless Sensor Networks[J]. Journal of Electronics & Information Technology, 2022, 44: 1-13. doi: 10.11999/JEIT221193 [2] Hoang D T, Niyato D, Wang P, et al. Performance Analysis of Wireless Energy Harvesting Cognitive Radio Networks Under Smart Jamming Attacks[J]. IEEE Journal on Selected Areas in Communications, 2015, 1(2): 200-216. [3] Jung H, Van Nguyen B, Song I, et al. Design of Anti-Jamming Waveforms for Time-Hopping Spread Spectrum Systems in Tone Jamming Environments[J]. IEEE Transactions on Vehicular Technology, 2019, 69(1): 728-737. [4] Popper C, Strasser M, Capkun S. Anti-Jamming Broadcast Communication Using Uncoordinated Spread Spectrum Techniques[J]. IEEE Journal on Selected Areas in Communications, 2010, 28(5): 703-715. doi: 10.1109/JSAC.2010.100608 [5] Hanawal M K, Abdel-Rahman M J, Krunz M. Joint Adaptation of Frequency Hopping and Transmission Rate for Anti-Jamming Wireless Systems[J]. IEEE Transactions on Mobile Computing, 2015, 15(9): 2247-2259. [6] Nutzinger M, Fabian C, Marschalek M. Secure Hybrid Spread Spectrum System for Steganography in Auditive Media[C]//2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing. Piscataway: IEEE, 2010. [7] Purwar A, Joshi D, Chaubey V K. GPS Signal Jamming and Anti-Jamming Strategy—a Theoretical Analysis[C]//2016 IEEE Annual India Conference(INDICON). Piscataway: IEEE, 2016. [8] Jia L L, Xu Y H, Sun Y M, et al. Stackelberg Game Approaches for Anti-Jamming Defence in Wireless Networks[J]. IEEE Wireless Communications, 2018, 25(6): 120-128. doi: 10.1109/MWC.2017.1700363 [9] Yao F Q, Jia L L. A Collaborative Multi-Agent Reinforcement Learning Anti-Jamming Algorithm in Wireless Networks[J]. IEEE Wireless Communications Letters, 2019, 8(4): 1024-1027. doi: 10.1109/LWC.2019.2904486 [10] Pirayesh H, Zeng H. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey[J]. IEEE Communications Surveys & Tutorials, 2022, 24(2): 767-809. [11] 朱行涛, 刘郁林, 栗铁桩. 基于循环平稳差异的直扩信号盲提取抗干扰方法[J]. 电子学报, 2017, 45(6): 1506-1512. doi: 10.3969/j.issn.0372-2112.2017.06.032Zhu Xing-tao, Liu Yu-lin, Li Tie-zhuang. Anti-jamming Method by Blindly Extracting of Direct Sequence Spread Spectrum Signal Based on Cyclostationary Difference[J]. Acta Electronica Sinica, 2017, 45(6): 1506-1512. doi: 10.3969/j.issn.0372-2112.2017.06.032 [12] Zhang Y S, Zhu W G, Yin C B, et al. Direct Sequence Spread Spectrum Communication Narrowband Interference Cancelation in Compressed Domain[J]. Transactions on Emerging Telecommunications Technologies, 2020, 31(6): e3830. [13] Quan H, Zhao H, Cui P Z. Anti-jamming Frequency Hopping System Using Multiple Hopping Patterns[J]. Wireless Personal Communications, 2015, 81(3): 1159-1176. doi: 10.1007/s11277-014-2177-1 [14] 王俊, 赵宏志, 卿朝进, 等. 同时同频全双工场景中的射频域自适应干扰抵消[J]. 电子与信息学报, 2014, 36(6): 1435-1440.Wang Jun, Zhao Hong-zhi, Qing Chao-jin, et al. Adaptive Self-interference Cancellation at RF Domain in Co-frequency Co-time Full Duplex Systems[J]. Journal of Electronics & Information Technology, 2014, 36(6): 1435-1440. [15] Luo S X, Zhang S, Ke S, et al. Optimum Combining for Coherent FFH/DS Spread Spectrum Receivers in the Presence of Multi-Tone Jammer[J]. IEEE Access, 2020, 8: 53097-53106. doi: 10.1109/ACCESS.2020.2980858 [16] Abdulkawi A, Saleh T S, Khattab S, et al. Anti-jamming Defense in Wireless Networks Using Channel Hopping And Error Correcting Code[C]//2012 8th International Conference on Informatics and Systems(INFOS). Piscataway: IEEE, 2012. [17] 张道成. 基于空域滤波的 GPS抗干扰算法仿真及性能评估[J]. 指挥控制与仿真, 2019, 41(3): 85-87. doi: 10.3969/j.issn.1673-3819.2019.03.018Zhan Dao-cheng. Anti-jamming Algorithm Simulation and Evaluation Performance of GPS Based on Spatial-domain Filter[J]. Command Control & Simulation, 2019, 41(3): 85-87. doi: 10.3969/j.issn.1673-3819.2019.03.018 [18] 甘泉, 孙学军, 唐斌. 一种基于空域滤波的空间谱估计方法[J]. 信号处理, 2010, 26(2): 3100-3106.Gan Quan, Sun Xue-jun, Tang Bin. A Spatial Spectrum Estimation Method Based on the Spatial Filtering Approach[J]. Signal Processing, 2010, 26(2): 3100-3106. [19] 王俊, 赵宏志, 马万治, 等. 同时同频全双工宽带射频自干扰抵消性能分析[J]. 通信学报, 2016, 37(9): 121-130. doi: 10.11959/j.issn.1000-436x.2016184Wang Jun, Zhao Hong-zhi, Ma Wan-zhi, et al. Performance Analysis of Broadband Self-Interference Cancellation at RF Domain in Co-Frequency Co-Time Full Duplex Systems[J]. Journal on Communications, 2016, 37(9): 121-130. doi: 10.11959/j.issn.1000-436x.2016184 [20] Choi Y S, Shirani-Mehr H. Simultaneous Transmission and Reception: Algorithm, Design and System Level Performance[J]. IEEE Transactions on Wireless Communications, 2013, 12(12): 5992-6010. doi: 10.1109/TWC.2013.101713.121152 [21] Lee J. Self-Interference Cancelation Using Phase Rotation in Full-Duplex Wireless[J]. IEEE Transactions on Vehicular Technology, 2013, 62(9): 4421-4429. doi: 10.1109/TVT.2013.2264064 [22] 程莉, 李峥嵘, 黎杨, 等. 基于 MIMO系统的判别性信道估计技术研究[J]. 现代电子技术, 2022, 45(13): 41-44.Cheng Li, Li Zheng-rong, Li Yang, et al. Research on Discriminative Channel Estimation Technology Based on MIMO System[J]. Modern Electronics Technique, 2022, 45(13): 41-44. [23] 李汀, 张春洁, 夏雨婷. 超大规模混合场 MIMO去伪峰信道估计技术[J/OL]. 信号处理. [2022-12-10]. http://kns.cnki.net/kcms/detail/11.2406.TN.20221107.1748.006.html. [24] 殷敬伟, 张晓, 赵安邦, 等. 时间反转镜在水声通信网上行通信中的应用[J]. 哈尔滨工程大学学报, 2011, 32(1): 1-5. doi: 10.3969/j.issn.1006-7043.2011.01.001Yin Jing-wei, Zhang Xiao, Zhao An-bang, et al. The Application of a Virtual Time Reversal Mirror to Upstream Communication of Underwater Acoustic Networks[J]. Journal of Harbin Engineering University, 2011, 32(1): 1-5. doi: 10.3969/j.issn.1006-7043.2011.01.001 [25] 赫彬, 苏洪涛. 认知雷达抗干扰中的博弈论分析综述[J]. 电子与信息学报, 2021, 43(5): 1199-1211. doi: 10.11999/JEIT200843He Bin, Su Hong-tao. A Review of Game Theory Analysis in Cognitive Radar Anti-jamming[J]. Journal of Electronics & Information Technology, 2021, 43(5): 1199-1211. doi: 10.11999/JEIT200843 [26] Jia L L, Yao F Q, Sun Y M, et al. Bayesian Stackelberg Game for Antijamming Transmission with Incomplete Information[J]. IEEE Communications Letters, 2016, 20(10): 1991-1994. doi: 10.1109/LCOMM.2016.2598808 [27] Lmater M A, Haddad M, Karouit A, et al. Smart Jamming Attacks in Wireless Networks During a Transmission Cycle: Stackelberg Game with Hierarchical Learning Solution[J]. International Journal of Advanced Computer Science and Applications, 2018, 9(4): 358-360. [28] Jia L, Xu Y, Sun Y, et al. A Game-Theoretic Learning Approach for Anti-Jamming Dynamic Spectrum Access in Dense Wireless Networks[J]. IEEE Transactions on Vehicular Technology, 2019, 68(2): 1646-1656. doi: 10.1109/TVT.2018.2889336 [29] Zhang Y L, Xu Y H, Xu Y T, et al. A Multi-Leader One-Follower Stackelberg Game Approach for Cooperative Anti-Jamming: No Pains, No Gains[J]. IEEE Communications Letters, 2018, 22(8): 1680-1683. doi: 10.1109/LCOMM.2018.2843374 [30] Han C, Niu Y T. Cross-layer Anti-Jamming Scheme: A Hierarchical Learning Approach[J]. IEEE Access, 2018, 6: 34874-34883. doi: 10.1109/ACCESS.2018.2847045 [31] Yao F Q, Jia L L, Sun Y, et al. A Hierarchical Learning Approach to Anti-Jamming Channel Selection Strategies[J]. Wireless Networks, 2019, 25(1): 201-213. doi: 10.1007/s11276-017-1551-9 [32] Wang X M, Xu Y H, Chen C H, et al. Machine Learning Empowered Spectrum Sharing in Intelligent Unmanned Swarm Communication Systems: Challenges, Requirements and Solutions[J]. IEEE Access, 2020, 8: 89839-89849. doi: 10.1109/ACCESS.2020.2994198 [33] Zhao C Y, Wang Q, Liu X F, et al. Reinforcement Learning Based a Non-Zero-Sum Game for Secure Transmission Against Smart Jamming[J]. Digital Signal Processing, 2021, 112: 103002. doi: 10.1016/j.dsp.2021.103002 [34] Liu S Y, Xu Y F, Chen X Q, et al. Pattern-aware Intelligent Anti-Jamming Communication: A Sequential Deep Reinforcement Learning Approach[J]. IEEE Access, 2019, 7: 169204-169216. doi: 10.1109/ACCESS.2019.2954531 [35] Nasir Y S, Guo D. Multi-agent Deep Reinforcement Learning for Dynamic Power Allocation in Wireless Networks[J]. IEEE Journal on Selected Areas in Communications, 2019, 37(10): 2239-2250. doi: 10.1109/JSAC.2019.2933973 [36] Yang H L, Xiong Z H, Zhao J, et al. Intelligent Reflecting Surface Assisted Anti-Jamming Communications: A Fast Reinforcement Learning Approach[J]. IEEE Transactions on Wireless Communications, 2020, 20(3): 1963-1974. [37] Liu X, Xu Y H, Jia L L, et al. Anti-Jamming Communications Using Spectrum Waterfall: A Deep Reinforcement Learning Approach[J]. IEEE Communications Letters, 2018, 22(5): 998-1001. doi: 10.1109/LCOMM.2018.2815018 [38] Li K, Jiu B, Liu H W, et al. Reinforcement Learning Based Anti-Jamming Frequency Hopping Strategies Design for Cognitive Radar[C]//2018 IEEE International Conference on Signal Processing, Communications and Computing(ICSPCC). Piscataway: IEEE, 2018. [39] Xu J L, Lou H X, Zhang W F, et al. An Intelligent Anti-Jamming Scheme for Cognitive Radio Based on Deep Reinforcement Learning[J]. IEEE Access, 2020, 8: 202563-202572. doi: 10.1109/ACCESS.2020.3036027 [40] 宋佰霖, 许华, 蒋磊, 等. 一种基于深度强化学习的通信抗干扰智能决策方法[J]. 西北工业大学学报, 2021, 39(3): 641-649. doi: 10.3969/j.issn.1000-2758.2021.03.022Song Bai-lin, Xu Hua, Jiang Lei, et al. An Intelligent Decision-Making Method for Anti-Jamming Communication Based on Deep Reinforcement Learning[J]. Journal of Northwestern Polytechnical University, 2021, 39(3): 641-649. doi: 10.3969/j.issn.1000-2758.2021.03.022 [41] Bi Y, Wu Y, Hua C Q. Deep Reinforcement Learning Based Multi-User Anti-Jamming Strategy[C]//CC 2019-2019 IEEE International Conference on Communications(ICC). Piscataway: IEEE, 2019. [42] Nguyen C T, Van Huynh N, Chu N H, et al. Transfer Learning for Future Wireless Networks: A Comprehensive Survey[J]. Proceedings of the IEEE, 2021, 110(8): 1073-1115. [43] Chen G H, Zhan Y J, Chen Y, et al. Reinforcement Learning Based Power Control for in-body Sensors in WBANs Against Jamming[J]. IEEE Access, 2018, 6: 37403-37412. doi: 10.1109/ACCESS.2018.2850659 [44] Han C, Niu Y T. Multi-regional Anti-Jamming Communication Scheme Based on Transfer Learning and Q Learning[J]. KSII Transactions on Internet and Information Systems (TIIS), 2019, 13(7): 3333-3350. [45] Lu X Z, Xiao L, Dai C H, et al. UAV-aided Cellular Communications with Deep Reinforcement Learning Against Jamming[J]. IEEE Wireless Communications, 2020, 27(4): 48-53. doi: 10.1109/MWC.001.1900207 [46] Saeed N, Celik A, Al-Naffouri T Y, et al. Localization of Energy Harvesting Empowered Underwater Optical Wireless Sensor Networks[J]. IEEE Transactions on Wireless Communications, 2019, 18(5): 2652-2663. doi: 10.1109/TWC.2019.2906309 [47] Akyildiz I F, Pompili D, Melodia T. State-of-the-art in Protocol Research for Underwater Acoustic Sensor Networks[C]//Proceedings of the 1st ACM International Workshop on Underwater Networks. New York, NY, USA: Association for Computing Machinery, 2006: 7-16. [48] Zhou M Z, Wang J F, Sun H X, et al. A Novel DNN Based Channel Estimator for Underwater Acoustic Communications with IM-OFDM[C]//2020 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Piscataway: IEEE, 2020. [49] 李斌, 郑思远, 曹秀岭, 等. 一种AUV移动OFDM水声通信系统设计[J]. 水下无人系统学报, 2018, 26(6): 612-617.Li Bin, Zhang Si-yuan, Cao Xiu-ling, et al. Design on Mobile OFDM Underwater Acoustic Communication System for an AUV[J]. Journal of Unmanned Undersea Systems, 2018, 26(6): 612-617. [50] Chen P, Rong Y, Nordholm S, et al. Compressed Sensing Based Channel Estimation and Impulsive Noise Cancelation in Underwater Acoustic OFDM Systems[C]// 2016 IEEE region 10 conference (TENCON). Singapore: IEEE, 2016. [51] 钟宏伟. 国外无人水下航行器装备与技术现状及展望[J]. 水下无人系统学报, 2017, 25(4): 215-225. doi: 10.11993/j.issn.2096-3920.2017.03.001Zhong Hong-wei. Review and Prospect of Equipment and Techniques for Unmanned Undersea Vehicle in Foreign Countries[J]. Journal of Unmanned Undersea Systems, 2017, 25(4): 215-225. doi: 10.11993/j.issn.2096-3920.2017.03.001 [52] 申中寅. 日本海洋实时监测系统DONET简介[J]. 国际地震动态, 2018(7): 34-40. doi: 10.3969/j.issn.0253-4975.2018.07.007Shen Zhong-yin. A Brief Introduction to DONET in Japan[J]. Recent Developments in World Seismology, 2018(7): 34-40. doi: 10.3969/j.issn.0253-4975.2018.07.007 [53] 李风华, 路艳国, 王海斌, 等. 海底观测网的研究进展与发展趋势[J]. 中国科学院院刊, 2019, 34(3): 321-330. doi: 10.16418/j.issn.1000-3045.2019.03.010Li Feng-hua, Lu Yan-guo, Wang Hai-bin, et al. Research Progress and Development Trend of Seafloor Observation Network[J]. Bulletin of Chinese Academy of Sciences, 2019, 34(3): 321-330. doi: 10.16418/j.issn.1000-3045.2019.03.010 [54] Shen Z Z, Wang S, Tan M, et al. Robotfish-based Underwater Mobile Sensor Networks for Environmental Monitoring[C]//The Fifteenth International Offshore and Polar Engineering Conference. Seoul, Korea: ISOPE, 2005. [55] Luo H J, Zhao Y Y, Guo Z W, et al. UDB: Using Directional Beacons for Localization in Underwater Sensor Networks[C]//2008 14th IEEE International Conference on Parallel and Distributed Systems. Melbourne, VIC, Australia: IEEE, 2008. [56] Luo H J, Guo Z W, Dong W, et al. LDB: Localization with Directional Beacons for Sparse 3D Underwater Acoustic Sensor Networks[J]. Journal of Networks, 2010, 5(1): 28-38. [57] Dou J F, Guo Z W, Cao J B, et al. Optimum Transmission Range for Underwater Acoustic Sensor Networks[C]// 2008 International Conference on Information Networking. Busan, Korea: IEEE, 2008. [58] Misra S, Singh R, Mohan S V R. Information Warfare-Worthy Jamming Attack Detection Mechanism for Wireless Sensor Networks Using a Fuzzy Inference System[J]. Sensors, 2010, 10(4): 3444-3479. doi: 10.3390/s100403444 [59] Sampath A, Dai H, Zheng H, et al. Multi-channel Jamming Attacks Using Cognitive Radios[C]//2007 16th International Conference on Computer Communications and Networks. Honolulu, USA: IEEE, 2007: 352-357. [60] Wu Y, Wang B, Liu K J R, et al. Anti-Jamming Games in Multi-Channel Cognitive Radio Networks[J]. IEEE Journal on Selected Areas in Communications, 2012, 30(1): 4-15. doi: 10.1109/JSAC.2012.120102 [61] Xu W, Trappe W, Zhang Y, et al. The Feasibility of Launching and Detecting Jamming Attacks in Wireless Networks[C]//Proceedings of the 6th ACM International Symposium on Mobile ad hoc Networking and Computing-MobiHoc’05. Urbana-Champaign, IL, USA: ACM Press, 2005: 46. [62] Zhu H J, Fang C L H, Liu Y, et al. You can Jam but You Cannot Hide: Defending Against Jamming Attacks for Geo-Location Database Driven Spectrum Sharing[J]. IEEE Journal on Selected Areas in Communications, 2016, 34(10): 2723-2737. doi: 10.1109/JSAC.2016.2605799 [63] Xiao L, Li Q D, Chen T H, et al. Jamming Games in Underwater Sensor Networks with Reinforcement Learning[C]//2015 IEEE Global Communications Conference (GLOBECOM). San Diego, USA: IEEE, 2015. [64] Xiao L, Jiang D H, Wang X Y, et al. Anti-Jamming Underwater Transmission with Mobility and Learning[J]. IEEE Communications Letters, 2018, 22(3): 542-545. doi: 10.1109/LCOMM.2018.2792015 [65] Xiao L, Jiang D H, Chen Y, et al. Reinforcement-learning-based Relay Mobility and Power Allocation for Underwater Sensor Networks Against Jamming[J]. IEEE Journal of Oceanic Engineering, 2020, 45(3): 1148-1156. doi: 10.1109/JOE.2019.2910938 [66] Su Y, Li L, Fan R, et al. A Secure Transmission Scheme with Energy-Efficient Cooperative Jamming for Underwater Acoustic Sensor Networks[J]. IEEE Sensors Journal, 2022, 22(21): 21287-21298. doi: 10.1109/JSEN.2022.3202169 [67] Zuba M, Shi Z, Peng Z, et al. Launching Denial-of-service Jamming Attacks in Underwater Sensor Networks[C]//Proceedings of the 6th International Workshop on Underwater Networks. New York, USA: Association for Computing Machinery, 2011: 1-5. [68] Yang G, Dai L, Wei Z. Challenges, Threats, Security Issues and New Trends of Underwater Wireless Sensor Networks[J]. Sensors, 2018, 18(11): 3907. doi: 10.3390/s18113907 [69] Stajano F. The Resurrecting Duckling[M]. Security Protocols. Berlin, Heidelberg: Springer, 2000. [70] Hu F, Wilson S, Xiao Y. Correlation-Based Security in Time Synchronization of Sensor Networks[C]//2008 IEEE Wireless Communications and Networking Conference. Las Vegas, USA: IEEE, 2008. [71] Xu M, Liu G, Zhu D, et al. A Cluster-Based Secure Synchronization Protocol for Underwater Wireless Sensor Networks-2014[EB/OL]. [2023-01-08]. https://journals.sagepub.com/doi/full/10.1155/2014/398610. [72] Pu C, Lim S, Jung B, et al. Mitigating Stealthy Collision Attack in Energy Harvesting Motivated Networks[C]// 2017 IEEE Military Communications Conference (MILCOM). Baltimore, USA: IEEE, 2017. [73] Kamalesh S, Kumar P G. Fuzzy Based Secure Intrusion Detection System for Authentication in Wireless Sensor Networks[J]. Journal of Computational and Theoretical Nanoscience, 2017, 14(5): 2465-2472. doi: 10.1166/jctn.2017.6247 [74] Fotohi R, Firoozi Bari S, Yusefi M. Securing Wireless Sensor Networks Against Denial-of-Sleep Attacks Using RSA Cryptography Algorithm and Interlock Protocol[J]. International Journal of Communication Systems, 2020, 33(4): e4234. [75] Pandarinath P. Secure Localization with Defense against Selective Forwarding Attacks in Wireless Sensor Networks[C]//2011 3rd International Conference on Electronics Computer Technology. Kanyakumari, India: IEEE, 2011: 112-117. [76] Ibragimov M, Lee J H, Kalyani M, et al. CCM-UW Security Modes for Low-band Underwater Acoustic Sensor Networks[J]. Wireless Personal Communications, 2016, 89(2): 479-499. doi: 10.1007/s11277-016-3283-z [77] Ahmed M R, Aseeri M, Kaiser M S, et al. A Novel Algorithm for Malicious Attack Detection in UWSN[C]//2015 International Conference on Electrical Engineering and Information Communication Technology(ICEEICT). Savar, Bangladesh: IEEE, 2015: 1-6. [78] Lim S, Huie L. Hop-by-Hop Cooperative Detection of Selective Forwarding Attacks in Energy Harvesting Wireless Sensor Networks[C]//2015 International Conference on Computing, Networking and Communications (ICNC). Garden Grove, CA, USA: IEEE, 2015: 315-319. [79] Jiang J, Han G, Zhu C, et al. A Trust Cloud Model for Underwater Wireless Sensor Networks[J]. IEEE Communications Magazine, 2017, 55(3): 110-116. doi: 10.1109/MCOM.2017.1600502CM [80] Saini M, Kaur R K. To Propose a Novel Technique for Detection and Isolation of Misdirection Attack in Wireless Sensor Network[J]. Indian Journal of Science and Technology, 2016, 9(28): 1-7. [81] Rathiga P, Sathappan S. Hybrid Detection of Black Hole and Gray Hole Attacks in MANET[C]//2016 International Conference on Computation System and Information Technology for Sustainable Solutions(CSITSS). Bengaluru, India: IEEE, 2016: 135-140. [82] Rani P, Kavita, Verma S, et al. Mitigation of Black Hole and Gray Hole Attack Using Swarm Inspired Algorithm with Artificial Neural Network[J]. IEEE Access, 2020, 8: 121755-121764. doi: 10.1109/ACCESS.2020.3004692 [83] Taylor V F, Fokum D T. Mitigating Black Hole Attacks in Wireless Sensor Networks Using Node-Resident Expert Systems[C]//2014 Wireless Telecommunications Symposium. Washington, DC, USA: IEEE, 2014: 1-7. [84] Guerroumi M, Derhab A, Saleem K. Intrusion Detection System against Sink Hole Attack in Wireless Sensor Networks with Mobile Sink[C]//2015 12th International Conference on Information Technology-New Generations. Las Vegas, NV, USA: IEEE, 2015: 307-313. [85] Zhang R, Zhang Y. Wormhole-Resilient Secure Neighbor Discovery in Underwater Acoustic Networks[C]//2010 Proceedings IEEE INFOCOM. San Diego, CA, USA: IEEE, 2010: 1-9. [86] Dargahi T, Javadi H H S, Shafiei H. Securing Underwater Sensor Networks against Routing Attacks[J]. Wireless Personal Communications, 2017, 96(2): 2585-2602. doi: 10.1007/s11277-017-4313-1 [87] Yavuz F, Zhao J, Yağan O, et al. On Secure and Reliable Communications in Wireless Sensor Networks: Towards k-connectivity under a Random Pairwise Key Predistribution Scheme[C]//2014 IEEE International Symposium on Information Theory. Honolulu, HI, USA: IEEE, 2014: 2381-2385. [88] Islam A A, Taher K A. A Novel Authentication Mechanism for Securing Underwater Wireless Sensors from Sybil Attack[C]//2021 5th International Conference on Electrical Engineering and Information Communication Technology(ICEEICT). Dhaka, Bangladesh: IEEE, 2021: 1-6. [89] Arifeen Md M, Al Mamun A, Ahmed T, et al. A Blockchain-Based Scheme for Sybil Attack Detection in Underwater Wireless Sensor Networks[C]//Proceedings of International Conference on Trends in Computational and Cognitive Engineering. Singapore: Springer, 2021: 467-476. [90] Li X, Han G, Qian A, et al. Detecting Sybil Attack Based on State Information in Underwater Wireless Sensor Networks[C]//2013 21st International Conference on Software, Telecommunications and Computer Networks - (SoftCOM 2013). [S.l.]: [s.n.], 2013: 1-5. [91] Chen H, Lou W. On Protecting End-To-End Location Privacy against Local Eavesdropper in Wireless Sensor Networks[J]. Pervasive and Mobile Computing, 2015, 16: 36-50. doi: 10.1016/j.pmcj.2014.01.006 [92] Shah D, Kumar V. TCP SYN Cookie Vulnerability[EB/OL]. [2022-12-16]. https://doi.org/10.48550/arXiv.1807.08026. [93] Maleki Sadr M A, Ahmadian-Attari M, Amiri R, et al. Worst-Case Jamming Attack and Optimum Defense Strategy in Cooperative Relay Networks[J]. IEEE Control Systems Letters, 2019, 3(1): 7-12. doi: 10.1109/LCSYS.2018.2850658 [94] Diamant R, Casari P, Tomasin S. Cooperative Authentication in Underwater Acoustic Sensor Networks[J]. IEEE Transactions on Wireless Communications, 2019, 18(2): 954-968. doi: 10.1109/TWC.2018.2886896 [95] Bagali S, Sundaraguru R. Efficient Channel Access Model for Detecting Reactive Jamming for Underwater Wireless Sensor Network[C]//2019 International Conference on Wireless Communications Signal Processing and Networking (WiSPNET). Chennai, India: IEEE, 2019. [96] Xu M, Liu G, Guan J. Towards a Secure Medium Access Control Protocol for Cluster-Based Underwater Wireless Sensor Networks[J]. International Journal of Distributed Sensor Networks, 2015, 11(5): 325474. doi: 10.1155/2015/325474 -




 下载:
下载: